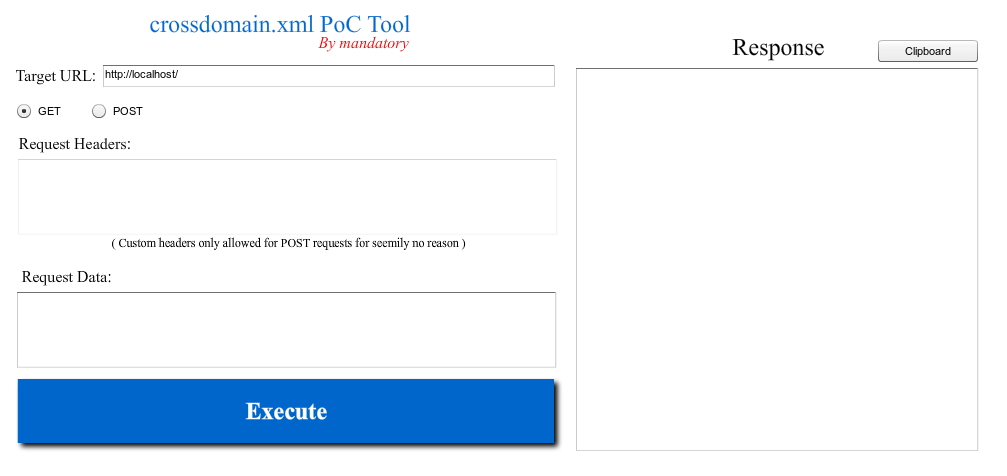
Cross Domain Hijacking
Ronan dunne ceh sscp security threat analyst soc engineer.
Cross domain hijacking. The content type of the response doesn t matter. Here is the attack scenario. Using websockets developers can exchange text and binary messages pushed from the server to the browser as.
However even after enabling frame content modification and disabling cross domain capture event i think you should disable frame content modification and enable cross domain capture event. Exploiting insecure file upload functionalities which do not check the file contents properly or allow to upload swf. This is a security measure designed to prevent malicious sites from hijacking content hosted by legitimate websites.
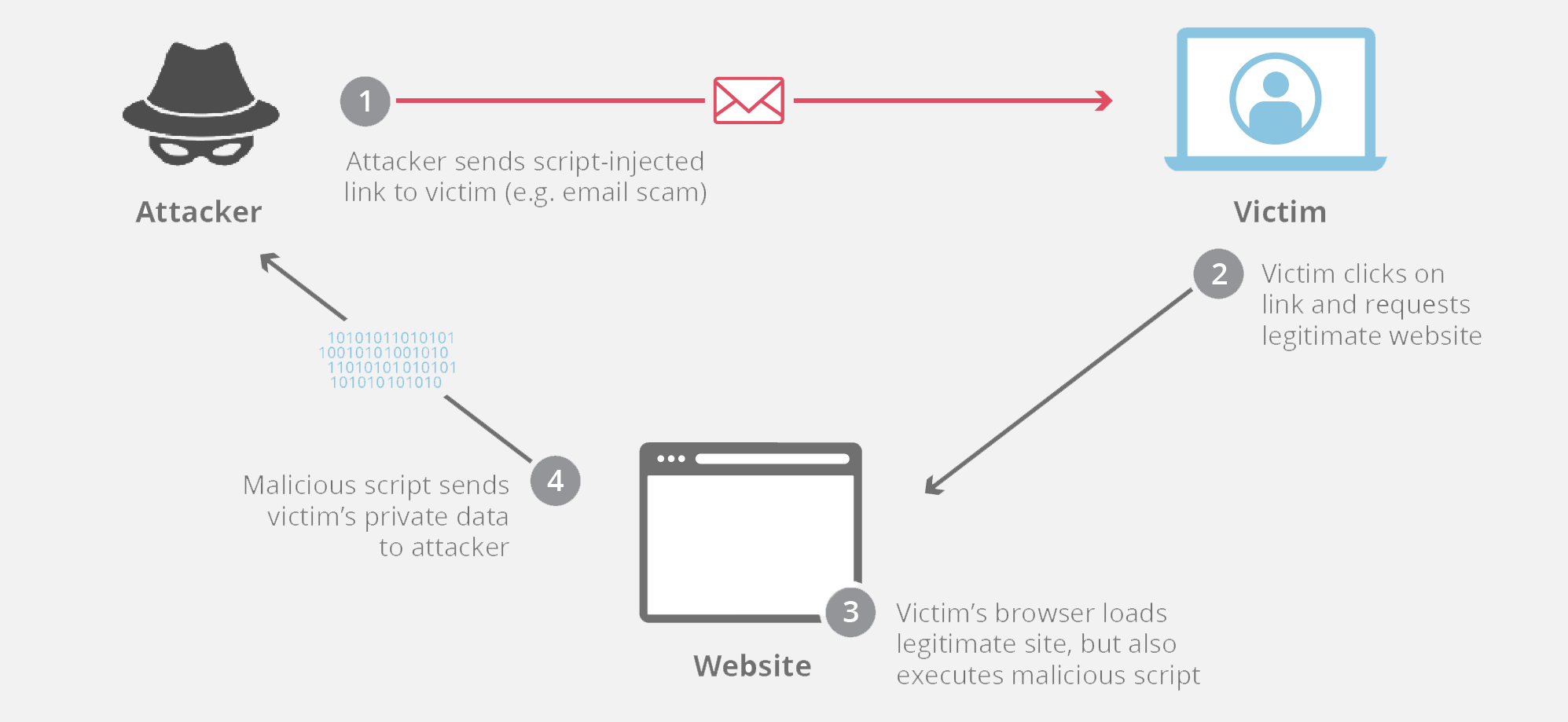
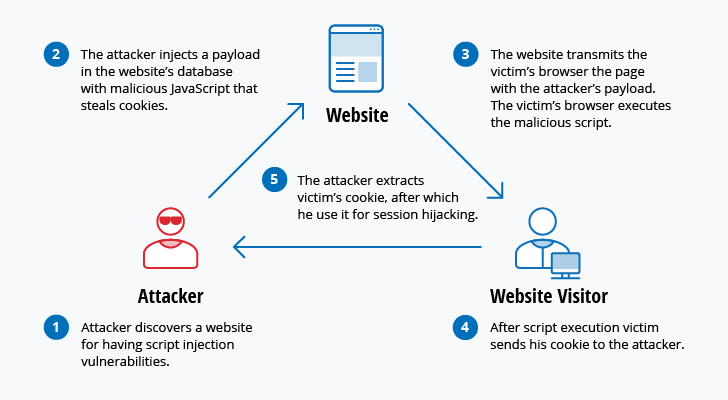
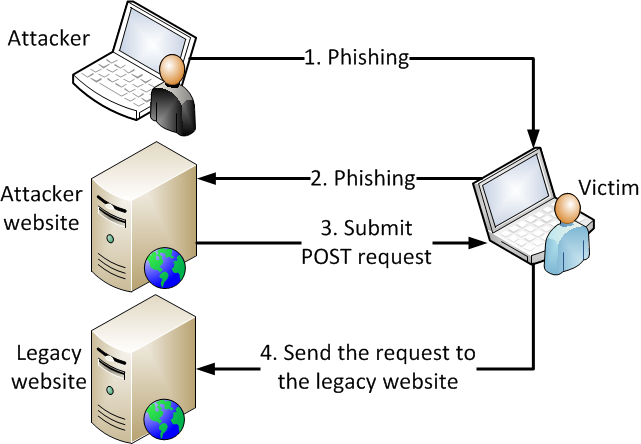
Cross site websocket hijacking also known as cross origin websocket hijacking involves a cross site request forgery csrf vulnerability on a websocket handshake. It arises when the websocket handshake request relies solely on http cookies for session handling and does not contain any csrf tokens or other unpredictable values. Update 3 01 11 2016 title was changed from cross domain data hijacking to cross site content hijacking to reflect the issue better.
Domain hijacking is a process by which internet domain names are stolen from their legitimate owners. This post is going to introduce a new technique that has not been covered previously in other topics that are related to file upload attacks such as unrestricted file upload and file in the hole. Cross domain hijacking file upload vulnerability 3 975 views.
Communicate with its source domain without checking the cross domain policy use the flash file to send requests and to read files from the domain of. This project can be used to provide a proof of concept for. However the cross domain server can permit reading of the response when credentials are passed to it by setting the cors access control allow credentials header to true.
Cross site content data hijacking xsch poc project. Cross site websocket hijacking cswsh the relatively new html5 websocket technique to enable full duplex communication channels between browsers and servers is retrieving more and more attention from developers as well as security analysts. The default behaviour of cross origin resource requests is for requests to be passed without credentials like cookies and the authorization header.